BUFFER OVERFLOW ATTACK TUTORIAL – EXAMPLE
Attacker would use a buffer-overflow exploit to take advantage of a program that is waiting on a user's input. There are two types of buffer overflows: stack-based ... GoldWave 6.43 Portable
buffer overflow attack tutorial by example
Attacker would use a buffer-overflow exploit to take advantage of a program that is waiting on a user's input. There are two types of buffer overflows: stack-based ... 82abd11c16 GoldWave 6.43 Portable
buffer overflow attack tutorial by example Worauf ist beim Erstellen eines Dienstplans zu achten
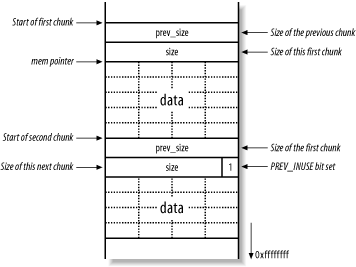
Buffer Overflow Attack on the main website for The OWASP Foundation. ... Below examples are written in C language under GNU/Linux system on x86 architecture. ... This very simple application reads from the standard input an array of the .... Learn how buffer overflow attacks work and how you can avoid them. ... Using this class is quite simple, for example, to extract all files from an .... Stack based Buffer Overflow Shellcode: The Payload Vulnerability & Exploit Examples Another BOF 'Research' This tutorial tries to investigate and proof the ... Samsung lanca leitor de e-book